With vulnerabilties being discovered all the time, configuring web servers to pass security checks is an ongoing process. (Another plate-spinning excercise.) The best free audit tool I know is https://www.ssllabs.com/ssltest/
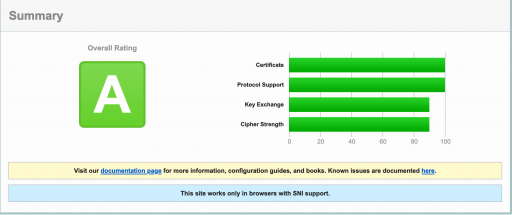
But that site won’t tell you how to configure your software. The configurator from mozilla https://ssl-config.mozilla.org/ does and has been invaluable to me as it covers all the types of services and versions of software you might be running.
An expert site for additional apache and nginx and IIS configuration is https://securityheaders.com/
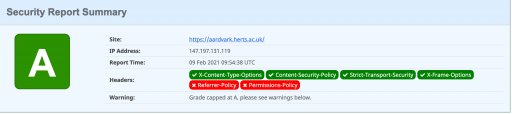
I think me making a hash of explaining these would be a mistake- anyway I’m going to run with these addition settings:
Header always set X-Content-Type-Options "nosniff"
Header always set Content-Security-Policy "default-src https: data: 'unsafe-inline' 'unsafe-eval'"
Header always set Strict-Transport-Security "max-age=31536000; includeSubDomains"
Header always set X-Frame-Options "SAMEORIGIN"
Header always set X-Xss-Protection "1; mode=block"
Referrer-Policy: strict-origin-when-cross-originWe should be worried in production that just bunging these lines without being sure of their consequences will cause side issues – so I guess we have to put it them into development and test like everything else.