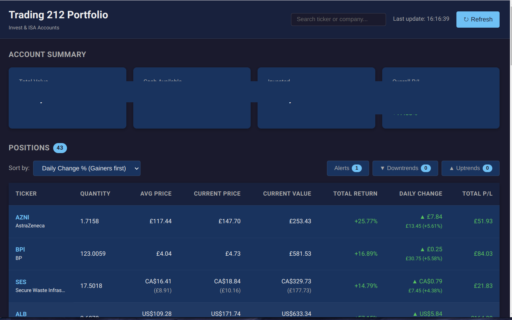
So inflation can be around 3% to 4% and how much do you get in your savings account. Well with trading212 you can invest in ETF’s and get 15% to 18% so get with it.
There is an api and I have had Claude write me a program to view it. It can’t compete with the phone App. It’s in Electron so updates if I put a new release out. Not really of much use. trading212 viewer